Cisco IT Essentials (ITE v6.0 + v7.0) Chapter 12 Exam Answers 100%
Cisco IT Essentials (ITE v6.0 + v7.0) Chapter 12 Exam Answers 100% – Join the growing IT workforce of tomorrow. Learn about the Cisco Networking Academy curriculum, learning platform, support & training.on healthyguide we provide solution to almost all exam answers today we provide anwers to cisco IT Essentials (ITE v6.0 + v7.0) Chapter 12 Exam Answers 100%.How to find ANSWER/QUESTION:
Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer.
Advertisement
NOTE: If you have a new question for this test, please leave a comment in the form below with the question and multiple-choice list. We will respond to your questions as soon as possible. Thank you very much! Your contribution to the website is greatly appreciated.
Related Articles
Cisco IT Essentials (ITE v6.0 + v7.0) Chapter 12 Exam Answers 100%
1. Which two location data sources can locator apps use to determine the position of a mobile device? (Choose two.)
- cellular towers
- WiFi hotspots
- the sandbox
- remote lock
- an app source
Explanation: In addition to GPS, mobile device locator apps can use cellular towers and WiFi hotspots to determine the position of a mobile device. The device sandbox, remote lock, or an app source (Play Store or iTunes) are other features and functions related to security and app downloading.
2. What are two ways that iOS differs from Android? (Choose two.)
- iOS uses an All Apps button whereas Android uses a Home button.
- iOS has a physical Home button, but Android uses navigation icons.
- In iOS, the icon for an app represents the app itself. Deleting the icon in iOS deletes the app. In Android, the icon on the Home screen is a shortcut to the app.
- In iOS, apps can only appear on screens, whereas in Android, apps can appear on screens and in folders.
- In iOS, folders are created by dragging one app on top of another app, but in Android folders must be created from the home screen menu.
Explanation: Apple iOS devices have a physical Home button that has many uses. One of the uses of the Home button is navigation between screens. Android uses navigation icons instead of a physical Home button. In addition, much like a Windows OS, apps in Android are represented by icons that are shortcuts to the actual app. In iOS, the icons are the apps. Deleting an icon in Android deletes only the shortcut. However, the entire app is deleted from an iOS device when its icon is deleted.
3. What are two purposes of the passcode lock feature on mobile devices? (Choose two.)
- to help prevent theft of private information
- to prevent unauthorized use of the device
- to erase all personal data from the device
- to return the device to the default factory state
- to restore and re-synchronize the device
- to remotely lock the device if it is stolen
Explanation: The passcode lock feature on mobile devices helps prevent theft of private information and places the device into a power saving state. Personal data will not usually be erased from some mobile devices unless the number of failed passcode login attempts exceeds a threshold. Remote lock allows the device to be locked from a remote location. A factory reset returns the device to the original operation state when the device was first purchased. Various applications such as email or cloud storage can provide synchronization capabilities to be able to restore and re-synchronize information such as user data, contacts, and email on a mobile device.y other device features and actions.
4. Refer to the exhibit. What two statements are true about the mobile operating system screen shown? (Choose two.)
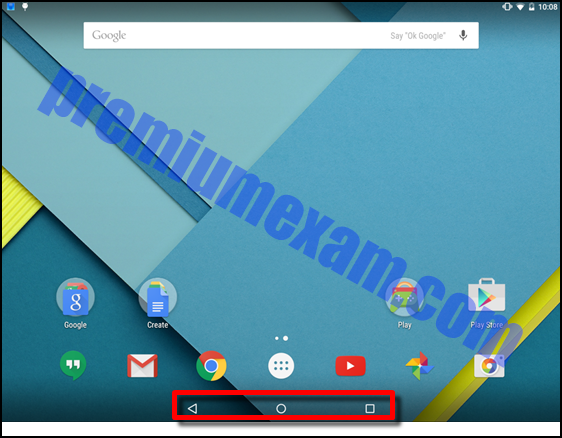
- The area enclosed by the red rectangle contains navigation icons.
- The area that is highlighted displays background processes and indicators.
- This is a Windows Phone screen.
- This is an Android screen.
- This is an iOS screen.
Explanation: The highlighted area shows the Android operating system navigation icons. From left to right they are Back, Home, and Recent Apps.
5. Which two methods are commonly used to remove the default restrictions and protections added to mobile operating systems? (Choose two.)
- rooting
- jailbreaking
- rootkit execution
- device update
- system backup
Explanation: Mobile operating systems are usually protected by a number of software restrictions. Rooting and jailbreaking are two methods for removing restrictions and protections added to mobile operating systems. They are a means of circumventing the usual operation of the device operating system to gain superuser or root administrator permissions.
6. A Linux administrator wants to backup current files in a data directory and store them in a new directory on another disk. Which two commands would be needed? (Choose two.)
- cd
- cp
- rm
- mv
- mkdir
Explanation: The mkdir command is used to create the new directory and the cp command is used to copy files from one directory to another.
7. A file called new_resume has the following file permissions: rw-r-x–x. What two facts can be determined from these permissions? (Choose two.)
- The user has full access to the file.
- Members of the group have read and execute access to the file.
- Other people have read and execute access to the file.
- Group members are able to modify the file.
- The user is able to read and modify the file.
- Other people have no access to the file.
Explanation: Read, write, and execute permissions are assigned to each file. The permissions are listed in groups of three. The first group of three permissions references users, the second references group members, and the third references others. The first position of each of the three permissions is the R or read permission, the second is the W or write permission, and the third is the X or execute permission. If any position has a dash, the associated group does not have permission for that category. In this case, the user hasread and write access (rw-). Group members haveread and execute access (r-x). Other people haveexecute only access (–x).
8. What is a good source for safely downloading Android apps?
- iTunes
- Google Play
- freeware sites
- the Apple App Store
Explanation: Google Play ensures that the app is compatible with the mobile device and is a trusted source for apps.
9. What represents apps in the Windows Phone interface?
- buttons
- icons
- tiles
- widgets
Explanation: The Windows Phone OS uses tiles to represent apps. Tiles are rectangles that can display active content. When tapped, they open the associated app. Tiles can be resized to unclutter screens and to reflect the relative importance of the app.
10. What is the result of doing a factory reset on a mobile device?
- The operating system will be updated with the most recent updates and patches.
- All user data and settings will be deleted.
- The operating system will be deleted and all user data is transferred to the Cloud.
- A complete backup of the device is done and all viruses and malware are removed.
Explanation: After a factor reset, a mobile device is left in the same state that it was when it left the factory. The operating system software would not be altered but all user data, settings, and third party applications would be deleted. Backups should be done prior to a factory reset. Updates or patches to the operating system could be done before or after the factory reset.
11. What is the name of the Windows Phone 8.1 digital, or virtual, assistant?
- Bing
- Cortana
- Nova Launcher
- Spotlight
Explanation: Siri is the well-known digital, or virtual, assistant that is available in iOS. Windows Phone also has a digitial assistant. It is called Cortana.
12. What is Wi-Fi calling?
- a method used to push apps to smartphones
- a convenient way to securely and digitally make payments with mobile devices
- a government emergency alert service for smartphones
- a way to make mobile phone calls over a wireless data network
- a method for sharing data between two mobile devices
Explanation: Wi-Fi calling is a way that a mobile phone can use a wireless data network to make phone calls as if it were connected to a cellular network. In cases where cell phone coverage is inadequate, calls can be placed from places that have open Wi-Fi networks.
13. What is the purpose of signature files used to secure mobile devices and operating systems?
- They contain a record of historical and pending firmware and software updates.
- They contain a list of all user passwords.
- They contain a log of digital certificates and encryption keys associated with the user.
- They contain sample code from known viruses and malware that is used by security software to identify malicious software.
Explanation: Antivirus and antimalware software compare the contents of a disk with sample virus and malware code included in signature files. If a comparison is found, the user can be notified and the virus can be isolated or removed.
14. What is a purpose of the boot manager program?
- It manages antivirus signature files, encryption keys, and certificates when a device boots.
- It automates the POST and checks the disk for bad sectors during a boot.
- It checks the validity of hardware and software on the device after a factory reset.
- It allows the user to select the OS to use to boot the device.
- It allows the user to determine which apps are automatically opened during the boot process.
Explanation: Many devices have multiple operating systems installed in different partitions. When a device boots, the boot manager asks the user to select the OS to use. The boot manager then directs the BIOS to the correct partition so that the device can continue to boot by using the selected OS.
15. An administrator is re-imaging a large number of Mac OS X machines. What built-in tool or command can be used to remotely boot the computers?
- mstsc
- Netboot
- Time Machine
- Finder
Explanation: Netboot is a built-in tool on the Mac OS that allows for remotely booting the computers. Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file system. MSTSC is used to open the Windows Remote Desktop utility. Time Machine is an automatic backup utility built into the Mac OS.
16. What tool or command is used in the Mac OS X to navigate the file system?
- File Explorer
- Task Manager
- Finder
- mstsc
Explanation: Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file system. The mstsc command is used to open the Windows Remote Desktop utility. The Task Manager tool on Windows allows a user to view all running applications.
17. Which model does Apple use to provide iOS apps to customers?
- iCloud
- Xcode
- sandbox
- walled garden
Explanation: Apple uses a walled garden model for the iOS apps. The apps must be submitted to and approved by Apple before they are released to users.
18. Android apps run primarily based on privileges enabled by the user. Sometimes an Android app requires extra privileges to access system components. How do Android apps run to accomplish both situations?
- Android apps run in a sandbox.
- Android apps run in a guest mode.
- Android apps run in a walled garden.
- Android apps run through a proxy service.
Explanation: Android apps run in a sandbox and have only the privileges enabled by the user. If an app needs to obtain permissions, a prompt will appear and the user can grant permissions through settings.
19. Which navigation icon on the system bar of an Android device is used to return to the previous screen?
- Back
- Home
- Menu
- Recent Apps
Explanation: The Back icon, if pressed, returns to the previous screen.
20. Which statement describes the iOS app icons on a mobile device screen?
- Each icon is a shortcut of the app.
- Each icon represents the actual app.
- Each icon represents an instance of the actual app.
- Each icon links to multiple instances of the actual app.
Explanation: On the iOS interface, each app on screen is the actual app, not a shortcut.
21. What is the purpose of using the auto-brightness feature on a mobile device with an LCD screen?
- to conserve battery power
- to reduce the interference from sunlight
- to prevent the burn-in effect on the screen
- to display text messages with better contrast
Explanation: The LCD screen for most mobile devices uses the most battery power. Lowering the brightness or using the auto-brightness feature helps conserve battery power.
22. Which statement describes the Touch ID in iOS devices?
- It is used as the passcode.
- It is the encryption key set by the user.
- It is the hash value of the user fingerprint.
- It is used to set the touch screen sensitivity.
Explanation: Apple uses a technology known as Touch ID in which the user sets up a template fingerprint scan that is converted into a unique hash and stored within a secure cache on the iOS device. The hash is used to authenticate with the user.
23. Which cloud-based storage service does Microsoft provide for backups?
- iCloud
- Dropbox
- OneDrive
- Google Sync
Explanation: Data on mobile devices must be backed up periodically to ensure that it can be recovered if needed. Most mobile operating systems come with a user account linked to the cloud services of the vendor, such as iClould for iOS, Google Sync for Android, and OneDrive for Microsoft.
24. A mobile device user notices that the system update includes an update of the Primary Rate ISDN (PRI). What is the function of the PRI?
- It is the configuration of radio frequencies used on the device.
- It is the data rate setting of the user account with the carrier service.
- It is the configuration of the data rates between the device and the cell tower.
- It is the configuration information that the device needs to communicate on networks other than the carrier network.
Explanation: In addition to mobile operating system updates, there are two other types of updates for mobile device radio firmware. They are called baseband updates and consist of the Preferred Roaming List (PRL) and the Primary Rate ISDN (PRI). The PRL is configuration information that a cellular phone needs to communicate on networks other than the carrier network. The PRI configures the data rates between the device and the cell tower. This ensures that the device is able to communicate with the tower at the correct rate.
25. A Linux PC user notices that the PC freezes on startup and exhibits kernel panic where there is a stop screen. What is a possible cause for the issue?
- LILO has been deleted.
- GRUB has been corrupted.
- A driver has become corrupted.
- Deja Dup has been turned off in the system.
Explanation: When a driver in a Linux system has been corrupted or a piece of hardware is failing, the system will freeze on startup and exhibits kernel panic where there is a stop screen.
26. What command is used to open a text editor in a Linux system?
- grep
- ifconfig
- ls
- vim
Explanation: The vim command is used to open a text editor; ls displays files within a directory; grep searches for strings of characters within a file; and ifconfig displays information about the network interface card.
27. Which Linux file system introduced the journaled file system, which can be used to minimize the risk of file system corruption in the event of a sudden power loss?
- ext2
- ext3
- CDFS
- NFS
Explanation: The ext3 file system is considered a journaled file system that was designed to improve the existing ext2 file system. A journal, the main feature added to ext3, is a technique used to minimize the risk of file system corruption in the event of sudden power loss.
28. What is the most commonly used method to close an application that appears to be frozen on an OS X-based computer?
- Use Force Quit.
- Use Task Manager.
- Access the Status menu.
- Access the Notification Center.
Explanation: To use Force Quit, right-click on the application icon that is not responding from the Dock and close the application.
29. Which file system is the primary file system used by Apple in current Macintosh computers?
- ext2
- ext3
- CDFS
- HFS+
- APFS
Explanation: To use Force Quit, right-click on the application icon that is not responding from the Dock and close the application.
30. An instructor is discussing facts about different mobile device operating software. The instructor states: “The mobile devices have a feature called Spotlight that is a search tool that provides information from many sources.” To which OS does this relate: iOS, Android, or both?
- iOS
- Android
- both
31. An instructor is discussing facts about different mobile device operating software. The instructor states: “This OS uses the system bar, displayed at the bottom of every screen, to navigate apps and screens.” To which OS does this relate: iOS, Android, or both?
- Android
- iOS
- both
32. An instructor is discussing facts about different mobile device operating software. The instructor states: “This OS can be used by programmers to operate devices like laptops, smart TVs, and e-book readers.” To which OS does this relate: iOS, Android, or both?
- Android
- iOS
- both
33. An instructor is discussing facts about different mobile device operating software. The instructor states: “The icon on the Home screen is a shortcut to the app.” To which OS does this relate: iOS, Android, or both?
- Android
- iOS
- both
34. An instructor is discussing facts about different mobile device operating software. The instructor states: “WIFI hotspots are a location data source that can be used by locator apps to determine the position of a mobile device.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
35. An instructor is discussing facts about different mobile device operating software. The instructor states: “Remote backups are a cloud-enabled service for mobile devices.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
36. An instructor is discussing facts about different mobile device operating software. The instructor states: “GPS signals are used to enable geocaching, geotagging and device tracking on these mobile devices.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
37. An instructor is discussing facts about different mobile device operating software. The instructor states: “The start voice control function can be performed with the home button.” To which OS does this relate: iOS, Android, or both?
- iOS
- Android
- both
38. An instructor is discussing facts about different mobile device operating software. The instructor states: “To synchronize a mobile device to a PC, iTunes must be installed on the PC.” To which OS does this relate: iOS, Android, or both?
- iOS
- Android
- both
39. An instructor is discussing facts about different mobile device operating software. The instructor states: “When the device roams out of the range of any Wi-Fi networks, it can connect to the cellular data network if this feature is enabled.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
IT Essentials v6.0:
1. Which two security precautions will help protect a workplace against social engineering? (Choose two.)
- performing daily data backups
- encrypting all sensitive data stored on the servers
- registering and escorting all visitors to the premises
- ensuring that all operating system and antivirus software is up to date
- ensuring that each use of an access card allows access to only one user at the time
2. Which two characteristics describe a worm? (Choose two.)
- executes when software is run on a computer
- is self-replicating
- hides in a dormant state until needed by an attacker
- infects computers by attaching to software code
- travels to new computers without any intervention or knowledge of the user
3. Which type of security threat uses email that appears to be from a legitimate sender and asks the email recipient to visit a website to enter confidential information?
- adware
- phishing
- stealth virus
- worm
4. What is the primary goal of a DoS attack?
- to facilitate access to external networks
- to prevent the target server from being able to handle additional requests
- to obtain all addresses in the address book within the server
- to scan the data on the target server
5. Which type of attack involves the misdirection of a user from a legitimate web site to a fake web site?
- SYN flooding
- DDoS
- DNS poisoning
- spoofing
6. Which password is the strongest?
- qwerty
- Abc123
- Im4ging!
- Gd^7123e!
- pAssword
7. Which three questions should be addressed by organizations developing a security policy? (Choose three.)
- What assets require protection?
- How should future expansion be done?
- What is to be done in the case of a security breach?
- When do the assets need protecting?
- What insurance coverage is required?
- What are the possible threats to the assets of the organization?
8. The XYZ company has decided to upgrade some of its older PCs. What precaution should the company take before the disposal of the remaining older computers?
- Perform a high-level format of the hard drive.
- Remove the RAM from the motherboard.
- Data wipe the hard drive.
- Destroy the monitor.
- Remove the CPU.
9. Which two file-level permissions allow a user to delete a file? (Choose two.)
- Read
- Modify
- Read and Execute
- Write
- Full Control
- List Contents
10. What is the name given to the programming-code patterns of viruses?
- grayware
- mirrors
- signatures
- virus definition tables
11. What is the most effective way of securing wireless traffic?
- WPA2
- SSID hiding
- WEP
- wireless MAC filtering
12. Port triggering has been configured on a wireless router. Port 25 has been defined as the trigger port and port 113 as an open port. What effect does this have on network traffic?
- Any traffic that comes into port 25 allows outgoing port 113 to be used.
- All traffic that is sent into port 25 to the internal network will also be allowed to use port 113.
- Any traffic that is using port 25 going out of the internal network will also be allowed to transmit out port 113.
- All traffic that is sent out port 25 will open port 113 to allow inbound traffic into the internal network through port 113.
13. What are two physical security precautions that a business can take to protect its computers and systems? (Choose two.)
- Perform daily data backups.
- Implement biometric authentication.
- Lock doors to telecommunications rooms.
- Replace software firewalls with hardware firewalls.
- Ensure that all operating system and antivirus software is up to date.
14. What is the minimum level of Windows security required to allow a local user to restore backed up files?
- Write
- Read
- Create
- Full
15. What is the purpose of the user account idle timeout setting?
- to log a user out of a computer after a specified amount of time
- to display a timeout message if a user has not typed a keystroke in a particular amount of time
- to turn the computer off if the user has not typed anything after a specified amount of time
- to create a log message of how long the computer was not used
16. Which two security procedures are best practices for managing user accounts? (Choose two.)
- Disable authentication.
- Limit the number of failed login attempts.
- Restrict the time of day that users can log into a computer.
- Enable AutoRun.
- Enable port forwarding.
17. Which Windows Firewall option allows the user to manually allow access to the ports required for an application to be allowed to run?
- Manage Security Settings
- Automatically
- Turn off Windows firewall
- Turn on Windows firewall
18. Which two Windows default groups are allowed to back up and restore all files, folders, and subfolders regardless of what permissions are assigned to those files and folders? (Choose two.)
- Administrators
- Power Users
- Backup Operators
- Access Control Assistants
- Cryptographic Operators
19. A manager approaches a PC repair person with the issue that users are coming in to the company in the middle of the night to play games on their computers. What might the PC repair person do to help in this situation?
- Limit the login times.
- Use Event View to document the times logged in and out of the computer.
- Use Device Manager to limit access to the computer.
- Enable power on passwords in the BIOS.
20. Which question would be an example of an open-ended question that a technician might ask when troubleshooting a security issue?
- Is your security software up to date?
- Have you scanned your computer recently for viruses?
- Did you open any attachments from a suspicious email message?
- What symptoms are you experiencing?
21. Which action would help a technician to determine if a denial of service attack is being caused by malware on a host?
- Disconnect the host from the network.
- Log on to the host as a different user.
- Disable ActiveX and Silverlight on the host.
- Install rogue antivirus software on the host.
22. A technician is troubleshooting a computer security issue. The computer was compromised by an attacker as a result of the user having a weak password. Which action should the technician take as a preventive measure against this type of attack happening in the future?
- Check the computer for the latest OS patches and updates.
- Verify the physical security of all offices.
- Ensure the security policy is being enforced.
- Scan the computer with protection software.
23. It has been noted that the computers of employees who use removable flash drives are being infected with viruses and other malware. Which two actions can help prevent this problem in the future? (Choose two.)
- Set virus protection software to scan removable media when data is accessed.
- Configure the Windows Firewall to block the ports that are used by viruses.
- Disable the autorun feature in the operating system.
- Repair, delete, or quarantine the infected files.
- Enable the TPM in the CMOS settings.
24. A virus has infected several computers in a small office. It is determined that the virus was spread by a USB drive that was shared by users. What can be done to prevent this problem?
- Destroy the USB drive.
- Activate Windows Firewall.
- Change the passwords on the computers.
- Set the antivirus software to scan removable media.
25. A user is browsing the Internet when a rogue pop-up warning message appears indicating that malware has infected the machine. The warning message window is unfamiliar, and the user knows that the computer is already protected by antimalware software. What should the user do in this situation?
- Allow the software to remove the threats.
- Click the warning window to close it.
- Update the current antimalware software.
- Close the browser tab or window.
26. In what situation will a file on a computer using Windows 8.1 keep its original access permissions?
- when it is copied to the same volume
- when it is moved to the same volume
- when it is copied to a different volume
- when it is moved to a different volume
27. What security measure can be used to encrypt the entire volume of a removable drive?
- EFS
- TPM
- BitLocker To Go
- NTFS permission
28. A user calls the help desk reporting that a laptop is not performing as expected. Upon checking the laptop, a technician notices that some system files have been renamed and file permissions have changed. What could cause these problems?
- The file system is corrupted.
- The laptop is infected by a virus.
- The display driver is corrupted.
- The file system has been encrypted.
29. Which two operating systems can be upgraded to Windows XP Home? (Choose two.)
- Windows 95
- Windows 3.1
- Windows 98
- Windows 98 SE
- Windows NT workstation
30. A customer using a Windows XP computer is complaining that a new card reader is not working. A technician tests the card reader on a Windows 7 computer and does not detect any problems. What are two possible solutions to the problem with the XP computer? (Choose two.)
- Install additional RAM.
- Modify the options in the BIOS.
- Install the driver from the CD provided with the card reader.
- Download and install the driver from the manufacturer of the card reader.
- Update the CMOS firmware.
31. A technician is replacing an internal hard drive used as a secondary drive on a PC. After connecting the new hardware and powering up the computer, an “OS not found” error message is displayed. What is the most probable cause for that error message?
- The power supply is faulty.
- The hard drive jumper is set incorrectly.
- The motherboard needs replacing to be able to support the new hard drive.
- The USB port has too many attached devices to supply adequate power.
- The BIOS needs updating.
32. A technician is upgrading an older PC with a dual core CPU. When the PC restarts, it is slower than it was before the upgrade. The Performance tab from the Task Manager displays only one CPU graph. What is the most probable solution to this problem?
- Replace the HDD with a higher capacity hard drive.
- Overclock the CPU.
- Increase the amount of RAM available.
- Update the BIOS firmware to support the dual core CPU.
33. A laptop that is running Windows XP displays “Missing NTLDR” after the POST. What are the two most probable reasons for this problem? (Choose two.)
- Boot.ini is missing or damaged.
- There is a conflict with a newly installed device.
- BOOTMGR has been corrupted.
- The boot order is not set correctly in the BIOS.
- The index service is not indexing in the correct locations.
34. Several times during the last few days, a user has experienced the Blue Screen of Death when plugging an external hard drive into a laptop via USB. What is a possible solution for this problem?
- Reinstall the operating system.
- Upgrade the operating system.
- Research the STOP error and the name of the module that produced the error.
- Research the boot error beep code to identify the source of the error.
35. A computer repeatedly locks without any error message. Which two conditions may be the cause of the problem? (Choose two.)
- The UAC has been turned off.
- The user has breached the user security policy.
- The computer has a virus.
- The index service is not running.
- The CPU needs to be upgraded.
- An update has corrupted the operating system.
36. What are two possible solutions to any Windows computer restarting continuously and never displaying the desktop? (Choose two.)
- Upgrade the processor.
- Upgrade the video card.
- Press F8 to open the Advanced Options menu and choose Disable Automatic Restart on System Failure.
- Reset the hard drive jumpers.
- Run chkdsk /F /R from the recovery console.
- Access the BIOS and change the boot order options.
37. A PC is not able to connect to a wired network. Pinging the loopback address is successful, but the gateway cannot be reached. On the network switch all the interface lights are on, except for the interface connected to the PC. The LED on the network card is off. What is the most likely cause of this problem?
- The network switch is faulty.
- The gateway needs to be fixed.
- The network cable is faulty.
- The PC has an incorrect IP address for the DNS server.
38. Users in a recently installed wireless network are complaining of slow data transfer and frequent loss of connectivity. The technician checks that the wireless security is correctly implemented, and there is no evidence of unauthorized users on the network. Which two problems might the technician suspect? (Choose two.)
- The wireless signal is too weak.
- The DHCP server is faulty.
- There is interference from outside sources.
- The antenna on the access point is too powerful.
- The network passwords need to be reissued to the users.
39. A group of users is unable to connect to the network. When testing several of the PCs and issuing the command ipconfig, the technician notices that all of them have an IP address in the 169.254.x.x range. What is the most likely cause of this problem?
- The DNS server is not operational.
- The Internet connectiion is down.
- The gateway address is incorrect.
- The DHCP server is not operational.
40. A technician is working on a laptop that has a dark display. After attaching an external display and verifying that it works, the technician now has a better idea as to the problem. What could be the problem?
- The display driver is incorrect.
- The motherboard has failed.
- The CPU has failed.
- The power inverter of the LCD screen or backlight lamp has failed.
41. A technician replaces a laptop keyboard that was no longer functioning, and has verified that the newly replaced keyboard functions properly. What is the final step the technician should take as part of the troubleshooting process?
- Ask a list of closed-ended questions.
- Research the problem.
- Document all findings, actions, and outcomes.
- Implement preventive measures.
42. A user complains that when a page is printed on a laser printer, the page smears when touched. What is a possible cause of this issue?
- The laser assembly is faulty.
- The EP drum is damaged.
- The pickup rollers are defective.
- The fuser has failed.
43. A technician finds that occasionally when a network printer is restarted, clients are unable to print to it, receiving a “Document failed to print” message. What is a probable cause of this?
- The drum is damaged.
- The printer does not have enough memory.
- The toner level in the EP cartridge is low.
- The power supply on the printer is failing.
- The printer is configured to get an IP address using DHCP.
44. A user complains that a printer is outputting random characters instead of the desired document. What is a probable cause of this?
- There is dirt or debris in the printer.
- The printer does not have enough memory.
- The pickup rollers are defective.
- An incorrect print driver is installed.
45. A freshly installed Windows 7 laptop is plugged into the network and configured with an IP address. The technician then attempts to ping the laptop from another computer. While the laptop is able to connect to other devices, the ping requests fail. What is the likely cause?
- The network drivers for the NIC are out of date.
- The port speed for the NIC is incorrect.
- TPM must be enabled.
- The Windows Firewall is blocking ping requests.
46. A computer displays this message when the computer boots: “MBR has been changed or modified.” What could cause this problem?
- The CMOS battery has failed.
- A RAM module is not fully inserted into the memory slot.
- A virus has altered the Windows kernel.
- A boot sector virus has altered the master boot record.
47. Users are complaining that they are receiving spam from the email account that belongs to a co-worker. What could cause this problem?
- A virus has damaged the master boot record on the system that is used by the co-worker.
- The network adapter on the computer that is used by the co-worker is malfunctioning.
- The email account belonging to the co-worker was hijacked because of malware.
- The email client belonging to the co-worker is not configured properly.
48. A technician is troubleshooting a laptop that has the power light on and the hard drive spinning. However, the laptop only displays vertical lines that change color. What is the problem?
- The BIOS is corrupt.
- The LCD screen has failed.
- The backlight lamp has failed.
- The LCD screen inverter has failed.
49. A technician is troubleshooting a laser printer that outputs blank paper for all print jobs including printer test pages. What is a probable cause?
- The laser printer does not have adequate memory.
- The drum is failing to hold a charge.
- The drum wiper blade is worn.
- The fuser has failed.
50. A technician arrives and asks a customer, “Can you describe the problem?” The customer replies, “All email messages that I send have the wrong date. I have restarted the computer several times, but this does not seem to help.”
What could be the problem?
- The MBR is corrupted.
- The CPU voltage is set too low.
- The CMOS battery has failed.
- The hard drive is beginning to fail.
51. A technician is troubleshooting a Windows 7 laptop infected with a virus that has damaged the master boot record. The technician has booted the laptop using the installation media and is attempting to repair the laptop from the command line interface. Which two commands can the technician use to repair the corrupt master boot record? (Choose two.)
- regedit
- chkdsk
- regedt32
- bootrec /fixboot
- bootrec /fixmbr
52. A file called new_resume has the following file permissions: rw-r-x–x . What two facts can be determined from these permissions? (Choose two.)
- Other people have no access to the file.
- Members of the group have read and execute access to the file.
- The user is able to read and modify the file.
- Group members are able to modify the file.
- Other people have read and execute access to the file.
- The user has full access to the file.







